This one is probably aimed more at the geekier end of the market, but it is an application well worth covering.
There are many reasons why you might want to capture the raw network traffic that is entering and leaving your system. This can be for diagnostic purposes when something has gone wrong, finding out if there's a rogue program on your network, or if you're just curious about what communications are going on.
Wireshark (formerly Ethereal) is one of the most well known free software packet capturing and analysis tools available. It is cross platform, and runs on Windows, Linux, Mac OS X and many other Unix-like operating systems.
A basic capture can be started by clicking the leftmost button on the toolbar and then selecting your primary network interface and clicking Start.
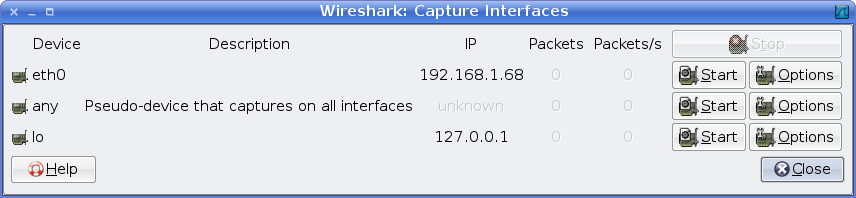
From that point on, Wireshark will capture all of the packets that are entering and leaving that interface. You can now get to work as normal, or do some action and come back and analyse the results later.
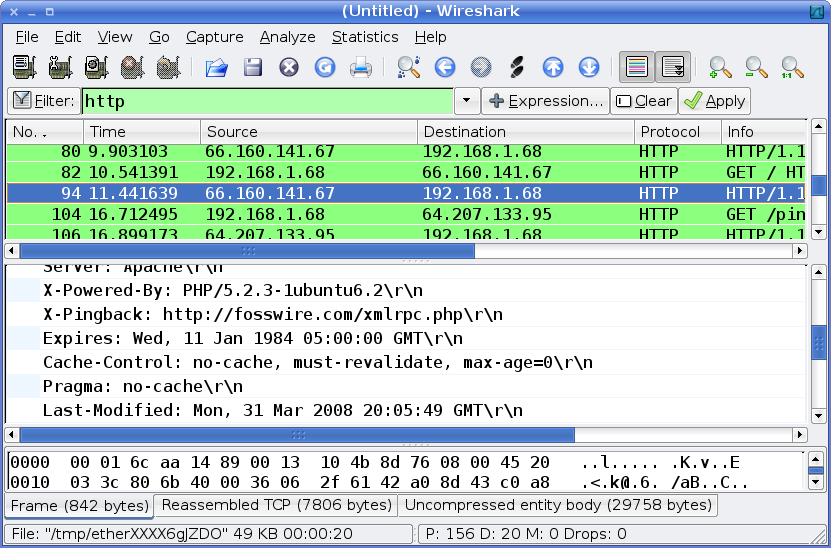
The analysis interface allows you to filter the packets by many criteria, including protocol, source, destination and many more powerful filters. You can then deconstruct what is going on by looking at the hex view, or on supported protocols, by looking at the data (such as the HTTP conversation in the screenshot above).
Packet dumps can then be saved to disk in libpcap format, and reopened in Wireshark or another program that supports the format.
Packet analysis isn't for the faint of heart, or for those who don't have some understanding of TCP/IP and other networking concepts. If you do like to delve a little deeper into what's going on network-wise, however, Wireshark is an invaluable tool and one of the best programs in its class.